Using PIA - Prevent Network Access Without VPN
Private Internet Access(PIA) is a great Virtual Private Network(VPN) service, but it does have some shortcomings that necessitate workarounds. One of those is where a Windows 10 PC/VM may connect to the Internet before PIA has established a secure VPN connection.
To work around this, we're going to configure Windows to not have an Internet gateway on bootup. That way it cannot connect to Internet before PIA starts. The PIA service will configure a temporary gateway through the VPN interface when it starts. It will also engage a kill switch in case the VPN connection breaks. Both of these tools will prevent your computer from inadvertently making an Internet connection including DNS requests.
Here is how I set it up on my Windows VM.
- Configure Windows to automatically login with non-admin account on bootup.
- Set a static IP and static DNS for the physical adapter. Leave the default gateway value empty.
- Configure PIA client to start on login
- Configure PIA client to automatically connect on startup
- Enable PIA kill switch
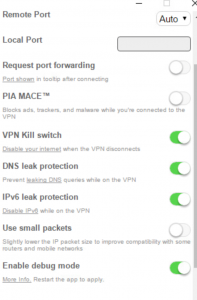
PIA Advanced Settings
PIA Advanced Settings
This is a rundown of what happens when you power on your PC.
- When windows boots up, it automatically logs in. I also have any apps that I want to run in the Windows 10 startup folder.
- The network adapter has local network access ( same subnet ) on boot up, but it doesn't have a way to route traffic to the Internet since the gateway it blank.
- You can access computers on your local network , but there is no Internet access
- PIA Starts.
- PIA reconfigures the physical network adapter to access the Internet on its own.
- PIA connects to the VPN gateway.
- The system now has local and Internet access.
- PIA Kill switch blocks Internet access when VPN disconnects.
I rebooted the test system 5 times, verifying that there was no Internet access before PIA started, and none after the VPN connection is terminated. I also made sure that no settings were lost during reboots.
Testing was done with:
- Windows 10 Professional install on a VMWare Guest on ESXI 6.5 host.
- PIA for Windows. I don't see a version number anywhere in the app, but at the time I installed it 7.5 was the current version.
I want to note that in this test configuration , your local DNS still works if you have one. In that case a DNS leak is possible. For example I have Pi-hole and Unbound DNS running on my local network . So I can still resolve Internet sites like "www.amd.com" to IP address even though I cannot connect to them directly.
What you can do is not use your ISP's DNS servers, use public DNS ( Google 8.8.4.4. 8.8.8.8 ) instead. You ISP would have to be sniffing your network packets for DNS requests to spy on what sites you are interested in.
I could not test for DNS leaks since the test system did not have access to any Internet leak tests sites. Also , the LOE to do it otherwise was out of scope for this post( ie I'm too lazy to do it :smiley: ).
I hope that this helps someone. Feel free to do further testing and add your experience / insights to this thread.